This post may contain affiliate links, meaning at no additional cost to you I may earn a small commission when you click a product or company link. As an Amazon Associate I earn from qualifying purchases.
How can you tell a legitimate email from a phishing email?
Several years ago when my husband and I were figuring out how we could afford to get married and go to graduate school at the same time, I received an email from someone claiming to be a professor at a university in Oklahoma.
The sender had a foreign-sounding name. The subject line was “Do you want to be a MacGyver?” And the email contents told me that if I joined this university’s super special secret agent computer security graduate degree program, I could earn lots of money while I was in school and basically be guaranteed employment after I graduated.
It kind of sounded too good to be true, and I almost deleted it. In fact, my husband-to-be told me, “Jess. It’s a phishing email! Just delete it and move on.”
Fortunately for both of us, I decided to do some research instead. And it turns out, the email was legitimate.
As a matter of fact, this email was the reason we were able to get married when we did. The program provided us with the means to continue our education and still have the financial resources to get married.
But how did I know the email was not a phishing email? And how can you identify phishing attempts?
Table of Contents
What is phishing?
First let’s talk for a minute about what a phishing email is. Phishing happens when a hacker sends you an email pretending to be from someone or something you trust (like your boss, your bank, a favorite shopping site, Google).
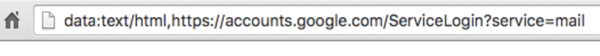
Phishing emails usually try to get you to click on a link and provide personal information, such as your credit card information, social security number, or username and password, like in this example.
The spoofed page looks legitimate and even has “accounts.google.com” in the browser bar. But notice the “data:text/html,” at the beginning of the address.
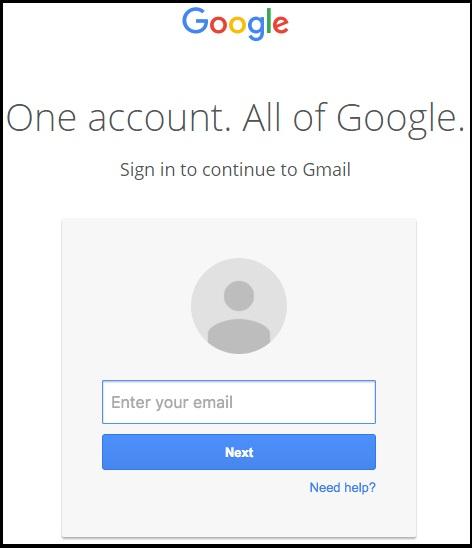
When you log in to the fake site, the hacker captures your information and is then able to log in to the *real* site as you.
Wonder how accounts get hacked? In an overwhelming majority of cases, this is how.
Detecting phishing emails
So how do you tell if that email you got is a phishing email?
Here are some things you can look for to protect yourself, your family, your devices, and your accounts:
Scare tactics
Phishing emails will often try to scare you into taking immediate action. For example, they may say, “Your account has been deactivated.” Or “We’ve noticed illegal activity in your account.” Or, “Re-enter your payment information before your account is terminated.”
If you’re scared about the status of your account or of being accused of something illegal, you may temporarily suspend judgment and login to “fix” the problem without checking to see if the email is legitimate.
Attachments
Not all attachments are bad, of course. My MacGyver email came with legitimate attachments! But this fact did increase my suspicion.
If you’re not expecting an attachment, you should be extra wary. If possible, it’s a good idea to confirm with the person that the email is supposedly from that they actually did send you an attachment. And don’t open it until you’re sure it’s legitimate!
Note that if you’re going to confirm an attachment, it’s a good idea to contact the person in some way *other than* the email address that the email came from. See this post for an example of a time when I responded to a “friend’s” email and got a hacker instead.
Sites, names, and links that look *almost* legitimate
One popular tactic when spoofing email addresses or websites is to use an address that looks almost like the real thing. For example, a phishing email from “Facebook” may come from admin@facebokaccounts.com. Or you may see something like “www.gma1l.com.”
Letters may be missing or substituted for similar characters, or you may see sites that sound legitimate but aren’t connected with the actual site.
If you’re not sure where a link goes, hover over it with your mouse to see the URL. (You can also right-click a link with your mouse and copy/paste it to examine it more closely.) On a mobile device, try holding down the link until the details pop up.
One simple way to protect yourself against these attacks is to use a password manager. In case you make a mistake and click on that link anyway, using something like LastPass can help prevent you from logging in on a phishing site. Your credentials will be saved for the correct domain (the web address), not the fake one. So when you visit a fake domain, the manager won’t provide your credentials.
Impersonal greetings
Hackers don’t always know who will receive their emails–they may be sending out a mass mailing just to see who bites. If the email is missing your name or username and just says something generic like, “Dear User,” you have reason for suspicion.
Misspellings or poor grammar
OK, so maybe the email is from your Aunt Liz’s email address, and she normally uses poor spelling or grammar… This check may not be foolproof. But generally speaking, phishing emails frequently come from non-native English speakers, and it tends to show in the writing. If it sounds or looks strange, it’s worth being cautious.
Some experts hypothesize that hackers don’t even try to make their emails sound sophisticated. Choppy, unpolished emails filter out the kinds of people who might get wise to the scam. Hackers are actively looking for people who aren’t paying attention to the details.
Being educated is key
Know what phishing emails look like. If you receive an email that you’re not sure about, either go directly to the website in question by typing the address into your browser’s address bar, or do some other independent research.
Don’t click links or attachments if you have any questions about an email!
When I got that strange MacGyver email, I went to the University of Tulsa’s website to see if there was actually a Professor Shenoi on the faculty. (There was; he was a professor of computer science, and he did, indeed, head up the Cyber Corps program.)
I did a Google search on the University of Tulsa’s Cyber Corps program and found details (including news articles) on the program that matched the information in the email. I checked the return email address and confirmed that it was actually to the University of Tulsa’s domain (utulsa.edu).
Everything lined up, so I hit “reply” and asked if there was room in the program for my soon-to-be fiance. The rest, as we say, is history.
Did you find this information useful? Please give me a share!