This post may contain affiliate links, meaning at no additional cost to you I may earn a small commission when you click a product or company link. As an Amazon Associate I earn from qualifying purchases.
Table of Contents
Is two-factor authentication just another buzzword?
You’ve probably heard the buzz about two-factor authentication and wondered what it was or if it was even relevant to you.
Does it really matter? Should you enable it? Is it anything more than just an annoyance?
So here’s the deal. Our entire lives are online, right? Not just our shopping accounts or social media, but our bank accounts, our kids’ medical records, and practically anything else you can think of.
We need to protect our lives online because of the huge crossover into our lives offline.
I’ve talked before about how to protect your accounts by creating passwords that hackers can’t guess, but what happens if they manage to get in anyway? Maybe your password wasn’t as secure as you thought. Or it was intercepted by a virus on your computer. Or you logged in on someone else’s computer and *that* computer had a virus.
There are any number of reasons your secure password might “fail” you. That’s why most important online accounts today will let you set up two-factor authentication. It’s all part of a bigger concept called defense in depth.
Defense in depth
This abstract includes a great analogy to banking–most banks have security cameras, security guards, bulletproof glass, electronically locked doors, vaults for valuables. All these defensive measures work together to create a more secure environment. If one fails, another is behind it to make sure the bank is not defenseless.
You can (and probably should) accomplish something similar with your online accounts by adding a second form of identification beyond just your password.
A simple definition
Two-factor authentication gets its name from the different “factors” you can use to identify yourself. The basic ones are
- something you know (such as a password or PIN)
- something you have (a physical key or a cell phone)
- something you are (a biological factor such as your fingerprint)
If you’ve ever used an ATM, you’ve used two-factor authentication. You withdraw cash (does anyone use cash anymore?) with something you have (your debit card) plus something you know (your PIN).
When I was working on sensitive work for previous employers, I used a variety of authentication measures, including ID cards, card readers, physical devices that generated random codes (like the one below), and personal PINs for entering secure spaces.

Why would the average person need two-factor authentication?
Obviously banks and sensitive work situations are one thing… But why would *you* ever want to set up two-factor authentication?
Remember that your email account is the gateway to all of your other accounts on the Internet. Arguably, it’s the gateway to your offline life too since our modern life is so connected. So at the very least I’d set up two-factor authentication on your email account and any account that involves money.
Related: Why You Probably Don’t Need Encrypted Email
What not to look for…
Do you remember several years ago when account providers would ask you to pick an image in addition to your password? Somehow it would supposedly keep your account more secure because hackers wouldn’t be able to guess your password AND what image you picked.
The problem is, choosing an image isn’t *true* multi-factor authentication. Remember the “something you know, something you have, something you are” list above? Well, a password and an image are both something you KNOW, so it’s really only the single “something you know” factor twice.
Or sometimes you have to provide a password plus a fact about yourself… Again, “your mother’s maiden name” or “the street you grew up on” is just something else you know. And easily researched.
If you’re with a bank that provides these options as their only “two-factor” solution, run. Far away. If that’s what security looks like to them, it’s likely only a matter of time before they’re hacked.
What to look for instead
What you want to look for instead is an account that lets you provide something you *have* or something you *are* in addition to your password.
In practice, this usually looks like an automated text message or phone call with a special code that you then enter on the website you’re logging into.
One of my husband’s colleagues specializes in cellphone network security. As my husband puts it, “He grits his teeth at the thought of authentication through text message.” Long story short, if you’re up against a persistent attacker, text messages are not sufficient.
The telephone networks just aren’t set up for true security. But it is better than nothing and will protect you in most cases.
Even better than a text message is an app on your phone that will generate a temporary code to use when you log in. You’ll need to sync the app with your account so that they both generate the same temporary code at the same time. (The Google Authenticator app is one such option.)
Troy Hunt’s article on the subject has a good explanation of why even an app on your phone may not be considered true two-factor authentication. But, again, for most everyday purposes, it is sufficient, and probably your best option.
How do you set up two-factor authentication?
Since most people I know use gmail, I’m going to walk you through setting up two-factor authentication with Google.
- Sign in to your gmail account and click on the icon that represents your account in the upper right-hand corner. Click the button that says, “Google Account.” This will take you to your account settings.
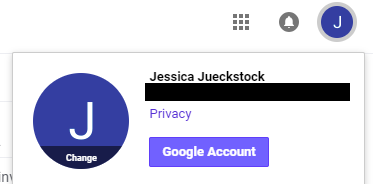
- On your account settings screen, click “Sign-in & security.”
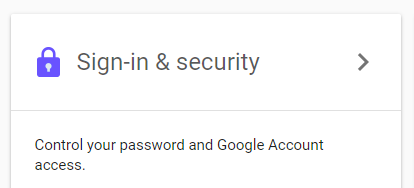
- Scroll down on this page, and you’ll see a section that says, “Password & sign-in method.” Below that you’ll see a setting that says, “2-Step Verification.” Click that.
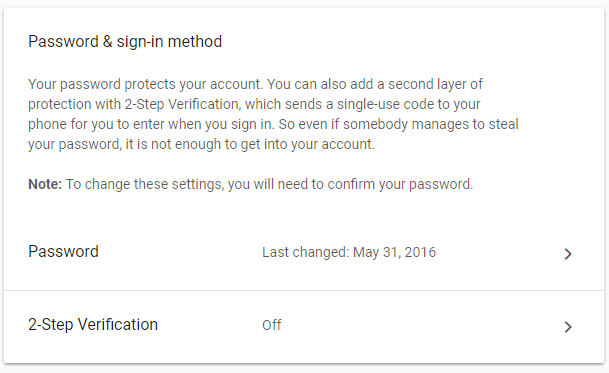
- Click “Get Started.” If you don’t see your phone listed on the next page, click, “Don’t see your device?” and follow the directions for connecting your phone to your account. Then click, “TRY IT NOW.”
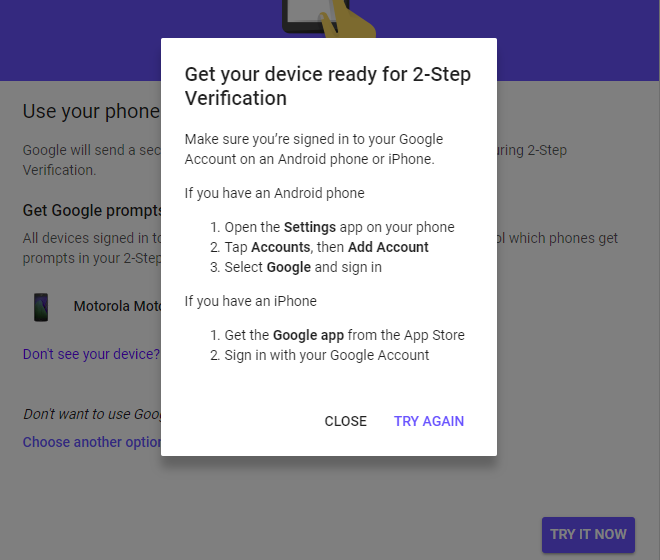
- You’ll see prompts to verify your phone and then add a phone number for backup. Follow the prompts and then click “TURN ON.”
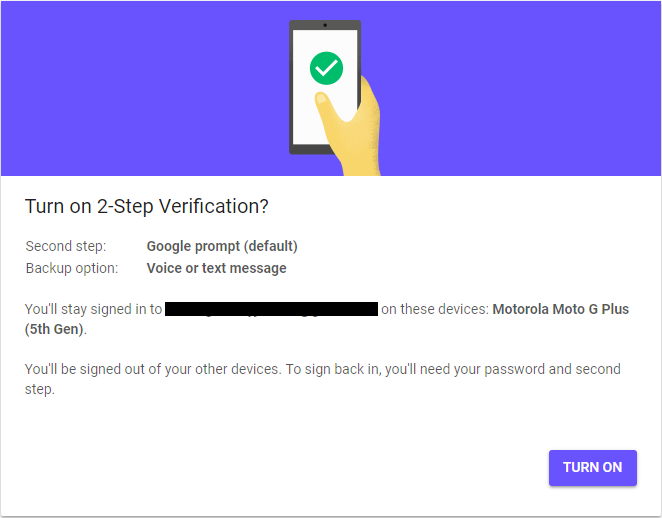
And that’s it! From the final page you can also select a different backup option, including a printed list of codes, the Authenticator app (which I mentioned above), and a physical security key (which I will go into in a future post).
Now whenever you log in to your account on a new device, you’ll need to have your phone with you (or one of the backup options) to verify that it’s you after you enter your password.
As always, if this was useful to you, I’d appreciate a share with your followers on social media!